How InvisiRisk BAF Effectively Mitigates GitHub Actions Supply Chain Attacks Like the Ultralytics/Action Compromise
- InvisiRisk, Inc.

- Mar 27, 2025
- 4 min read
Updated: Jan 20
Introduction
The rise of automation in software development has made CI/CD pipelines indispensable, with GitHub Actions standing out as a cornerstone for streamlining workflows. However, this reliance on automation introduces significant security risks, as demonstrated by the December 2024 supply chain attack on the Ultralytics project—a popular open-source AI library powering YOLO models. This incident, involving the `ultralytics/actions` GitHub Action, exploited CI/CD vulnerabilities through “script injection” and "pwn request" techniques, compromising official PyPI releases with cryptocurrency mining malware. Tracked as a critical supply chain vulnerability, this attack underscores the urgent need for robust security within CI/CD pipelines. In this blog post, we’ll dive into the mechanics and impact of the ultralytics/actions` attack and illustrate how InvisiRisk’s Build Application Firewall (BAF), with its proactive default security policies, could have thwarted this exploit, protecting development environments and sensitive data.
Brief Examination of the Ultralytics/Action Attack
The Ultralytics project, with over 33,000 GitHub stars and 60 million PyPI downloads, relies on GitHub Actions for its CI/CD processes, including the custom ultralytics/actions` action. In December 2024, attackers exploited this dependency to poison four PyPI releases (versions 8.3.41, 8.3.42, 8.3.45, and 8.3.46). Here’s a detailed breakdown of the attack vector and techniques employed:
Injection of Malicious Code: The attackers leveraged script injection technique which was reintroduced through a commit by crafting malicious pull requests (PRs) which executed shell commands when processed by an unsanitized workflow.

Figure 1: The commit of the workflow that reintroduced the vulnerability. 
Figure 2: Malicious pull request that has the script injection in the PR. (#18018) 
Figure 3: Malicious pull request that has the script injection in the PR. (#18020) Malicious Code Execution: The attack exploited the pwn request vulnerability like `pull_request_target` trigger in the `format.yml` workflow, allowing untrusted code from a forked PR to run in the privileged context of the base repository’s CI runner.

Figure 4: Unsanitized workflow using pull_request_target event. Downloading a Payload: The injected script from the PR used `curl` to fetch a malicious shell script (`file.sh`) from an external source (`raw.githubusercontent.com`), which is then executed within the CI environment.
Build Cache Poisoning and Secret Exfiltration: The script poisoned the build cache and exfiltrated API tokens, enabling the attacker to tamper with the build process and later upload malicious packages directly to PyPI, accessing secrets like the `GITHUB_TOKEN`.
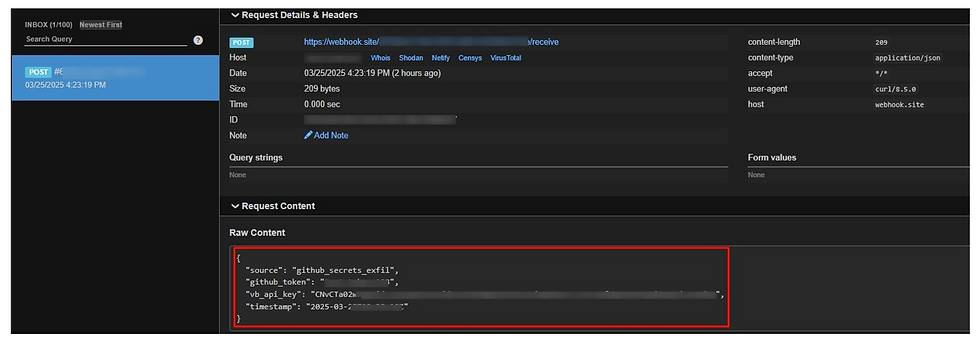
Figure 5: Recreated Secret leak for demonstration purpose. Payload Deployment: The compromised builds injected XMRig cryptocurrency mining code into Ultralytics’ `safe_download` and `safe_run` functions, affecting downstream users.
Objective: Supply Chain Compromise: The primary goal was to distribute malware via trusted PyPI packages, leveraging Ultralytics’ widespread adoption to maximize impact.
InvisiRisk BAF: A Real-Time and Layered Defense Strategy
InvisiRisk BAF is a cutting-edge security solution designed to fortify software build processes against supply chain attacks. It provides real-time protection through default security policies that block vulnerabilities, enforce trusted sources, and prevent unauthorized actions during builds. Among its out-of-the-box policies, the "Only Allows Trusted Package Registry" policy would have been pivotal in stopping the Ultralytics/action attack. Here’s how:
“Only Allows Trusted Package Registry” Policy: This core BAF policy restricts the sources from which dependencies and external resources can be retrieved during the build process, ensuring only approved registries are accessed.
Interception of External Requests: When the malicious script attempted to execute the `curl` command to download `file.sh` from `raw.githubusercontent.com`, BAF would have intercepted this network request. The BAF continuously monitors outbound traffic from the build environment to enforce its security rules.
Trusted Source Verification: BAF would have cross-checked `raw.githubusercontent.com` against its list of trusted sources. Given that this domain is not a standard package registry like PyPI or npm, it would fail the verification.
Blocking the Untrusted Request: Upon detecting an unapproved source, BAF would have blocked the `curl` request, preventing the connection and halting the download of the malicious script.

Figure 6: InvisiRisk BAF blocking malicious activity. Prevention of Malicious Code Execution: By stopping the payload retrieval and/or secret leak, BAF would have prevented the script from executing, thereby blocking cache poisoning, secret exfiltration, and the subsequent injection of XMRig into the build artifacts.
Mitigation of the Attack: The "Only Allows Trusted Package Registry" policy neutralizes the attack at the payload retrieval stage, ensuring the CI runner remains uncompromised and downstream packages stay clean.
Visualizing InvisiRisk BAF's Protective Mechanism

Lessons from the Ultralytics Attack
This incident highlights the fragility of CI/CD pipelines when untrusted inputs and external calls go unchecked. The reintroduction of a patched vulnerability (ultralytics/actions@c1365ce) in `ultralytics/actions` version 0.0.24, combined with poor workflow hygiene, opened the door to this attack. It’s a stark reminder that securing automation requires embedding protections directly into the build process. Solutions like InvisiRisk BAF offer a resilient shield against such threats by enforcing strict network controls and thwarting malicious payloads before they can execute.
Conclusion
The Ultralytics/action attack serves as a wake-up call for the open-source community, exposing how CI/CD exploitation via script injection and pwn requests can compromise even the most trusted projects. InvisiRisk BAF’s layered, real-time security—exemplified by its "Only Allows Trusted Package Registry" policy —would have stopped this attack in its tracks, protecting both the Ultralytics ecosystem and its vast user base. As supply chain threats evolve, adopting proactive defenses like BAF ensures that automation pipelines remain a strength, not a liability, in modern software development.



Comments